Efficient payment fraud prevention with crowd intelligence

Payment fraud is on the rise and its methods continue to evolve as technology advances and security measures improve. Safeguard your banking transactions with fast and easy vendor verification.
In this article, I will discuss some of the typical and less popular ways that fraudsters pose threat to business operations and outline a smart take on safeguarding both financial stability and long-term reputation for your organization.
Common methods of payment fraudsters in the B2B context are:
Phishing:
Phishing emails or text messages are sent to individuals, often impersonating reputable organizations, to trick them into revealing sensitive information like credit card numbers, login credentials, or personal information.
Identity theft:
Fraudsters steal personal information to pretend to be an employee or a manager of the organization to order payments to a fraudulent bank account.
Social engineering:
Fraudsters manipulate or trick individuals or employees into divulging sensitive information or performing actions that facilitate fraud. This can involve impersonation, pretexting, or baiting.
Business email compromise (BEC):
Scammers send fraudulent emails posing as a high-ranking executive or business partner to trick employees into transferring funds or sensitive information.
For effective payment fraud prevention, B2B companies need to establish and continuously improve best practices like segregating duties, strong legal contracts, employee training and security audits. Secondly, tools that provide email security, strong authorization procedures and secure payment channels must be used.
But to avoid payment fraud and wrongfully assigning payments to fraudulent bank accounts effectively vendor risk assessment and most importantly the verification of vendors and respective bank accounts are of highest priority.
Vendor verification is a must
Verifying vendors is a critical aspect of due diligence in a business-to-business (B2B) context. Proper vendor verification helps reduce the risk of fraud, ensures that you're working with reliable partners, and helps protect your organization's interests.
While some steps require manual effort and additional activities (e.g. business documents review, litigations or legal issues check, financial statements check, relevant industry certification or contractual agreements checks, asking for references, visiting vendor’s location etc.), others can be applied in an automated manner.
Here are steps to best verify vendors:
Check legal entity status:
Verify that the vendor is a legally registered entity by checking their business registration with relevant government agencies. This might include verifying their business license, tax identification number, and articles of incorporation.
Verify bank information:
Verify the vendor's bank account information. Ensure that the vendor provides accurate banking details, and cross-check them with the information you have on file. This helps prevent fraudulent payments.
Background checks:
Depending on the nature of your relationship with the vendor, consider conducting background checks on key personnel, especially if they will have access to sensitive data or financial information. (learn more about screening against PEP lists)
Periodic reassessment:
Vendor verification is not a one-time process. Periodically reassess your vendors to ensure they continue to meet your criteria for reliability, security, and performance.
Use Third-Party Services:
You can also consider using third-party services that specialize in vendor verification and due diligence. These services can provide in-depth reports and analysis.
By implementing these measures, businesses can reduce the risk of falling victim to B2B bank transaction fraud and maintain the security of their financial operations. However, the measurements described above include lots of manual reviews to authenticate the vendor and its associated accounts. This is not only very time-consuming but also will not be able to keep up with the rise of new technology like Artificial Intelligence used by fraudsters.
For instance, with the rise of voice imitations and deep fake videos, phone calls are considered traditionally a time-intensive but reliable source of information cannot be trusted anymore. Lastly, investing many hours into vendor verification becomes even less cost-effective for business relationships that are not of high stakes or volumes. This calls for higher levels of automation in vendor verification.
Automate vendor verification
Automating vendor verification can streamline the process, save time, and reduce the risk of human error. Here are steps and strategies to automate vendor verification:
Centralize data management:
Establish a centralized database or software system to store and manage vendor information. This system should include vendor profiles, documents, and due diligence records.
Vendor self-service portals:
Implement self-service portals where vendors can submit and update their information, ideally verified against trusted sources, e.g. business register. This reduces the administrative burden on your team and ensures that vendor data is up-to-date.
API integrations:
Integrate your vendor management system with external data sources, such as government databases, financial institutions, and credit agencies, to automatically validate and update vendor information.
Validation rules:
Define validation rules and algorithms within your system to verify vendor information, such as tax identification numbers or business registration details, in real-time. Flag discrepancies for further review.
Regular data updates:
Schedule automated data updates and validations at regular intervals, ideall in real time, to ensure that vendor information remains accurate and current.
Continuous monitoring:
Set up continuous monitoring systems that can flag and trigger alerts for any changes in a vendor's status or compliance.
Automated alerts and notifications:
Set up automated alerts and notifications for key events, such as when a vendor's documentation is about to expire or when a vendor's financial status changes.
Integration with compliance databases:
Integrate with compliance databases and watchlists to automatically screen vendors against sanctions lists, politically exposed persons (PEP) databases, and other regulatory lists.
Compliance automation:
Leverage compliance management software to automate regulatory compliance tasks, such as Anti-Money Laundering (AML) and Know Your Customer (KYC) checks.
Risk scoring models:
Develop risk-scoring models that automatically assess the risk associated with each vendor based on various factors, including financial stability, regulatory compliance, and past performance.
Additional approaches and methods for streamlining vendor verification encompass:
- Automated document collection: Use document capture and recognition tools to automatically extract relevant information from documents provided by vendors. Optical Character Recognition (OCR) technology can be helpful in this process.
- Machine learning and AI: Implement machine learning and artificial intelligence (AI) algorithms to detect anomalies and unusual patterns in vendor data that might indicate potential fraud or non-compliance.
- Automated due diligence workflows: Create automated workflows for due diligence processes. For example, if a vendor's risk score exceeds a certain threshold, an automated workflow can be triggered for a more in-depth review.
- Artificial intelligence in document verification: Utilize AI-driven document verification services to verify the authenticity and accuracy of documents submitted by vendors.
- Advanced analytics and reporting: Implement advanced analytics tools to generate reports and dashboards that provide insights into vendor performance, compliance, and risk trends.
Remember that while automation can significantly enhance the efficiency and accuracy of vendor verification, there should be mechanisms in place to review and address exceptions or anomalies that automated systems might not catch.
Additionally, the level of automation should be balanced with the specific needs and risks associated with your organization's vendor relationships. It's essential to stay informed about changing regulations and compliance requirements in your industry to ensure that your automated processes remain compliant.
Crowd Intelligence for the effective and secure payment fraud prevention
To keep up and stay ahead of payment fraudsters, CDQ established an expert community where good practices are shared, and equally important bank transaction data is shared. Whenever a new bank account is created or changed, the account information can be validated by the CDQ services responding with a “Bank Trust Score”. This score indicates how secure it is to use this account.
This is calculated on two main factors: successful payments already emitted by other community members that have the same vendor and the last date of the transaction. Transactions are only shared after a 90-day “cooling-off period”. The latter is important so that if a fraud attack does succeed, it can be detected and reported. All data is harmonized and anonymized by CDQ, thus the sharing companies are not displayed to the party requesting the bank trust score.
So whenever a new vendor’s bank details are being created or a change of the existing banking details is requested, the bank account validation service will immediately provide the trust score if the account is already in the shared pool or a fraud alert if any member of the community ever experienced a payment fraud attack associated with this specific account. The trust score can be adapted to each company's risk-based approach since thresholds can be maintained individually.
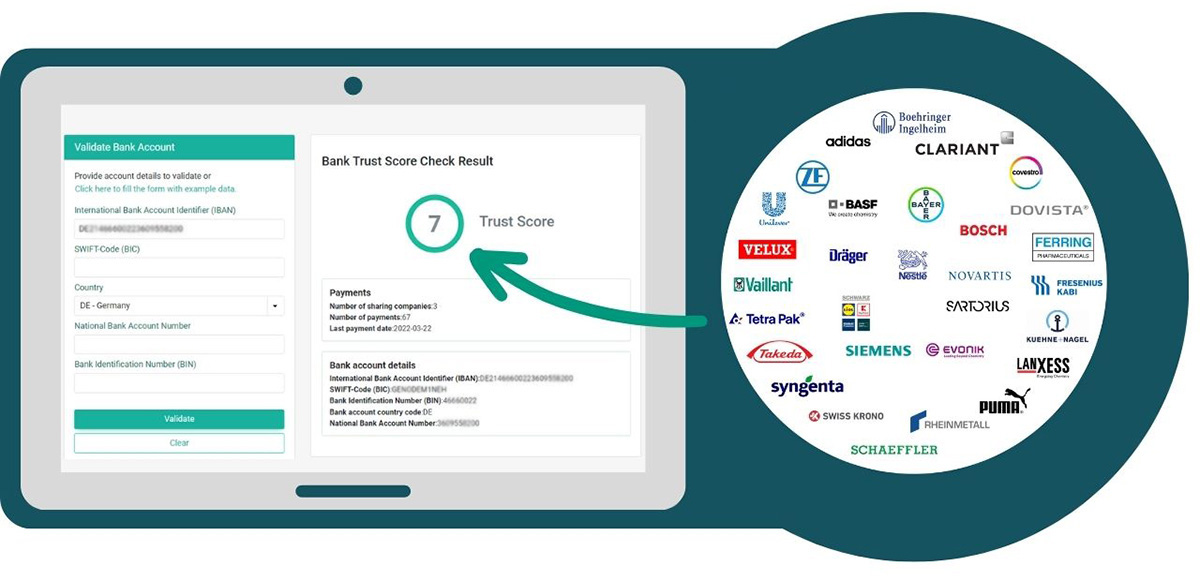
Summing up, the combination of shared data and shared knowledge from the expert community is the best counterfeiting against payment fraud. The CDQ-led Community gathered 1,7 million bank accounts with worldwide coverage, creating a superb database for vendor payment information verification thus successfully shielding businesses against fraud attacks and cybercriminals.
At CDQ we facilitate collaboration within smaller focus groups, including a Fraud Prevention working group, where we discuss and monitor the evolving fraud techniques with our community members from leading enterprises and stand strong together to safeguard your operations.
If you're interested in learning more about the crowd intelligence used at CDQ to help prevent payment fraud, please contact me directly via email or use a contact form below.

Get our e-mail!
Related blogs
Stepping out of silo thinking: Henkel’s data quality story
A refreshing look at how Henkel tackles an immensely complex data landscape: candid disussion with master data experts, Sandra Feisel and Stefanie Kreft.
The e-invoicing reality: the gateway is ready, but is your data?
Over the past decade, the EU has steadily shifted from encouraging electronic invoices to mandating them. And while the technology obviously plays an important…
A practical guide to managing regulatory compliance in business partner relationships
Regulatory compliance is complex and evolving. Not much of a surprise to anyone in today’s global business environment. Governments and international bodies…